-
COMMAND

Debunking IAM Myths: What You Should Know
Identity and Access Management (IAM) is essential for securing today’s digital organizations. It controls who can access systems and data,…
Read More » -
SECURITY

Smishing Scams Are on the Rise: How to Spot and
Text messages used to be a safe space—quick birthday wishes, delivery updates, maybe the odd emoji from a friend. But…
Read More » -
SERVER
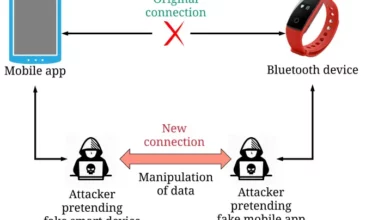
Bluetooth Vulnerability: Mitigating Risks Across Devices
I.Introduction Bluetooth has become an integral technology for billions of smartphones, computers, wearables, and other devices to connect and exchange…
Read More » -
SERVICES
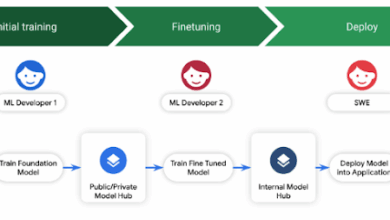
Practical Model Signing with Sigstore
In partnership with NVIDIA and HiddenLayer, as part of the Open Source Security Foundation, we are now launching the first…
Read More » -
UTILITIES
A Deep Dive into Impacket Remote Code Execution Tools
IMPACKET OVERVIEW Impacket was originally developed as a toolkit for penetration testing, providing security professionals with powerful capabilities to simulate…
Read More » -
NETWORKING
In search of a perfect enterprise Digital Asset Management system – Part 4 – Enterprise Digital Asset Management (DAM)
I do not have permission to download the files I want. Who can I get approval from? Many DAM…
Read More » -
SERVER

What does a good password policy really look like? — Matt Palmer
Passwords should be the easiest area of security. Every organisation has a password policy. Every organisation used passwords. Everyone at…
Read More » -
SERVICES
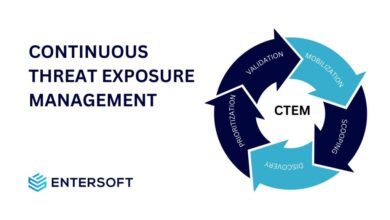
Harnessing Continuous Threat Exposure Management (CTEM) for Business Security
In the dynamic world of cybersecurity, Continuous Threat Exposure Management (CTEM) has emerged as a crucial approach for organizations seeking…
Read More » -
TIPS
Welcoming Aura to Have I Been Pwned’s Partner Program
One of the greatest fears we all have in the wake of a data breach is having our identity stolen.…
Read More » -
UTILITIES

Cybersecurity Advisory: Hackers Exploit Zoom’s Remote Control Feature
A newly uncovered cyberattack campaign is exploiting Zoom’s Remote Control feature to infiltrate the systems of cryptocurrency traders and venture…
Read More »