SECURITY
-
SECURITY
Scaling Sophos to $1B+ revenue and defending the 350M overlooked businesses
In this episode of Inside the Network, we sit down with Joe Levy, CEO of Sophos, a 40-year-old cybersecurity company…
Read More » -
SECURITY

Smishing Scams Are on the Rise: How to Spot and
Text messages used to be a safe space—quick birthday wishes, delivery updates, maybe the odd emoji from a friend. But…
Read More » -
SECURITY

Zero Trust Explained: Why Traditional
Let’s face it—cybersecurity is no longer a game of building taller walls or thicker locks. The old rules, the ones…
Read More » -
SECURITY
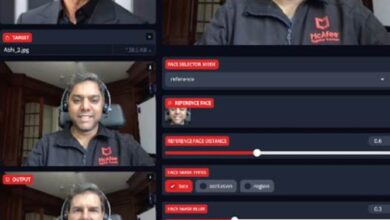
When AI Voices Target World Leaders: The Growing Threat of AI Voice Scams
If someone called you claiming to be a government official, would you know if their voice was real? This question…
Read More » -
SECURITY

10 immutable laws of security, 25 years later
Back in 2000, the Microsoft Security Response Center released an article titled “10 Immutable Laws of Security“, describing what they…
Read More »