-
TIPS

AI robots can now pass CAPTCHAs, and punch you in the face • Graham Cluley
In episode 62 of The AI Fix, your hosts learn how AI models smash through CAPTCHA roadblocks like they’re made…
Read More » -
SECURITY

Key Concepts in Digital Forensics & Cybersecurity
Cyberattacks don’t just hit networks. They hit trust. And once that’s gone, the road to recovery can be long and…
Read More » -
SERVICES
Invicti Platform Launch Research Team Update
One Engine to Rule Them All Our recent launch marked a significant achievement for Invicti, with the successful integration of…
Read More » -
TIPS
Welcoming Guardio to Have I Been Pwned’s Partner Program
I’m often asked if cyber criminals are getting better at impersonating legitimate organisations in order to sneak their phishing attacks…
Read More » -
COMMAND

What’s the Difference, and Why Does It Matter? · Riskonnect
The CER Directive and DORA are two major EU regulations focused on making organizations more resilient in different ways. But…
Read More » -
SECURITY
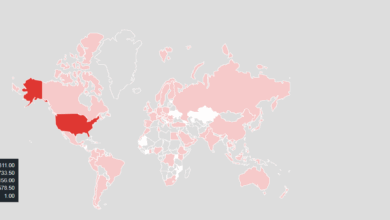
Think Before You Click: EPI PDF’s Hidden Extras
Authored by: Anuradha Prabudh PDF converting software can be super helpful. Whether you’re turning a Word document into a PDF…
Read More » -
UTILITIES

Scattered Spider Breached Allianz Life
Scattered Spider is on the news again – this time they breached Allianz Life. This week’s headlines range from ransomware-ready…
Read More » -
NETWORKING
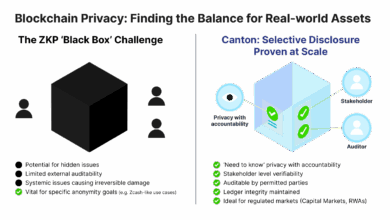
Why Institutions Need More Than Zero Knowledge
On April 16th 2025, Solana quietly patched a zero-day vulnerability in its Confidential Transfers feature — powered by zero-knowledge proofs…
Read More » -
SERVER
Comparing OAuth, OpenID Connect, and SAML
In today’s interconnected digital world, secure authentication is paramount to safeguarding user data and ensuring the integrity of web applications.…
Read More » -
SERVICES
What is BIMI | Brand Indicators for Message Identification
Why do even legitimate marketing emails get ignored? It’s not always the message it’s how the email looks. Years of…
Read More »