-
SERVER

From Asset Profile to Response: How Fidelis Accelerates MTTR
In cybersecurity, time isn’t just money, it’s everything. The longer it takes to detect and respond to an incident, the…
Read More » -
SERVICES

Why AI Prompt Injection Is the New Social Engineering
Why AI Prompt Injection Is the New Social Engineering Generative AI tools are becoming a major part of many business…
Read More » -
TIPS
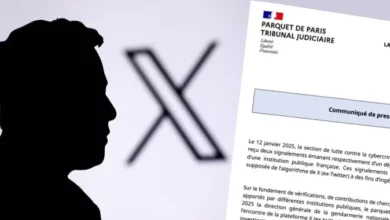
Quelle surprise! Twitter faces criminal probe in France • Graham Cluley
A criminal investigation into Twitter has been initiated by French prosecutors, over allegations that its algorithm is manipulated for the…
Read More » -
SECURITY
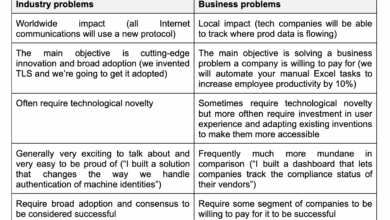
In security, not every industry problem is a business problem
Nobody can deny that there are many problems in our field. Just attend an industry conference or speak with five…
Read More » -
SERVER

The Only AI Tool AppSec Needs. Obviously
Software quietly runs the systems we rely on—our banks, logistics, communication, and cars. But for many AppSec teams, that software…
Read More » -
SERVICES

How Entersoft Empowers SEBI Entities in Cybersecurity & Resilience |
Introduction In an increasingly digital and interconnected world, cybersecurity for financial institutions is paramount. Recognizing this, the Securities and Exchange…
Read More » -
UTILITIES

Make Phishing Training Count with HootPhish
Stop tricking employees. Start training them. Take Control of Your Security Awareness Training with a Platform That’s as Effective as…
Read More » -
SECURITY

Black, White and Gray Box
Editor’s note: On the example of network security, Uladzislau describes the essence, pros and cons of black, gray, and white box…
Read More » -
SERVER

A Journey to the Highest Cybersecurity Maturity: Resources, Part 11
Resources Management Continue reading on The CISO Den »
Read More » -
TIPS

Choo Choo Choose to ignore the vulnerability • Graham Cluley
In episode 426 of the “Smashing Security” podcast, Graham reveals how you can hijack a train’s brakes from 150 miles…
Read More »