-
SERVER

Speeding Up Vulnerability Remediation Through Threat Correlation in XDR
In cybersecurity, speed matters. But so does clarity. When your organization is facing hundreds or thousands of known vulnerabilities, not…
Read More » -
SERVICES

Prompt Injection Attacks: Types, Risks and Prevention
Prompt Injection Attacks: Types, Risks and Prevention It’s no longer news that AI is changing how many businesses think. In…
Read More » -
SECURITY

Fake Job Interview Emails Installing Hidden Malware
Cyber criminals are becoming increasingly sophisticated, with a 60% rise in their use of deceptive tactics to infiltrate personal and…
Read More » -
SERVER

Why Nation-States Are Hacking the Power That Runs the World
“If you want to weaken a nation without firing a shot, start by flipping the switch.” Hello Cyber Builders 🖖,…
Read More » -
SERVICES

Black-Box vs White-Box Penetration Testing Explained
Introduction When securing your applications, choosing the right penetration testing methodology is crucial. Two widely used techniques are Black-Box Testing…
Read More » -
TIPS

Understanding Signaling System 7 (SS7)
The Signaling System 7 (SS7) is a set of protocol suite telecommunication networks used to share information across the global…
Read More » -
UTILITIES

Apple Alert: Critical AirPlay Vulnerabilities Expose Millions to Cyber Threats
A recent discovery by cybersecurity firm Oligo Security has unveiled a series of critical vulnerabilities in Apple’s AirPlay protocol and…
Read More » -
COMMAND
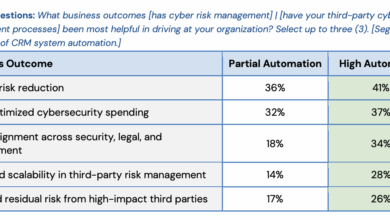
Key Insights from 2025 State of Cyber Risk Management Report
Join us for an exclusive deep dive into the groundbreaking findings from the FAIR Institute’s 2025 State of Cyber…
Read More » -
NETWORKING
AI company Hypergiant Industries snapped up by PE firm Trive Capital
Private equity firm Trive Capital has acquired Hypergiant Industries in a deal that will furnish the Texas-based AI company with…
Read More » -
SECURITY

What is DDoS attack: Types, signs, and how to
Companies face increasingly complex challenges every day, including cybersecurity threats aimed at disrupting their digital operations. One of the most…
Read More »