-
SERVER
My Story from the Spanish Blackout
Hello Cyber-Builders 🖖 In 2017, I published a paper with NATO experts on what had happened to the Ukrainian power…
Read More » -
UTILITIES

Are Creatives Fleeing Instagram Due to AI?
Meta admitted last month that it was using content posted to its flagship platforms Facebook and Instagram to train its…
Read More » -
COMMAND
Nick Sanna Keynote on FAIR Past & Future
If you’re looking to understand the rise of FAIR and acceptance of the quantitative approach to cyber risk management, you’ll…
Read More » -
NETWORKING

New Relic’s sale tells us much about the value of middling growth today
Monitoring service New Relic this morning said it has agreed to be acquired by Francisco Partners and TPG for $6.5…
Read More » -
SECURITY
You don’t start a platform, you earn the right to become one
In cybersecurity, “platform” is the most abused word, used by every startup with two engineers and a feature flag. We…
Read More » -
TIPS

Weekly Update 462
This will be the title of the blog post: "Court Injunctions are the Thoughts and Prayers of Data Breach Response".…
Read More » -
UTILITIES

20 Best Cybersecurity Business Ideas For Entrepreneurs
Are you looking for the best cybersecurity business ideas? We have got you covered. Read on! Over half a million…
Read More » -
COMMAND

How Vendor-Related Breaches Are Shaping Cybersecurity Strategies in 2025
The digital supply chain is central to operations in today’s business. Organizations depend on many third parties, such as cloud…
Read More » -
SECURITY
IoT Penetration Testing Strategy
Gartner expects more than 65% of enterprises (for reference, it was only 30% in 2017) to adopt IoT solutions by…
Read More » -
SERVER
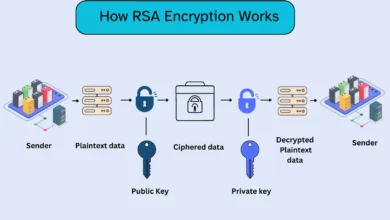
Enduring Power of RSA Encryption in Securing Network Communications
Introduction As organizations and individuals rely increasingly on digital systems to communicate and share sensitive information online, robust encryption methods…
Read More »