-
UTILITIES
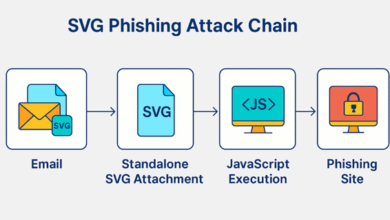
How Hackers Use Vector Graphics for Phishing Attacks
Introduction In the ever-evolving cybersecurity landscape, attackers constantly seek new ways to bypass traditional defences. One of the latest and…
Read More » -
SERVER
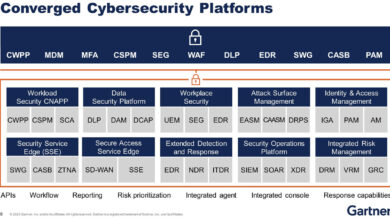
The 12 Cybersecurity Platforms That Define Modern Security
Hello, Cyber Builders 🖖 We’re continuing our deep dive into cybersecurity platforms. This is the third post in the series.…
Read More » -
TIPS

Weekly Update 459
New week, different end of the world! After a fleeting stop at home, we're in Japan for a proper holiday…
Read More » -
UTILITIES
NIST 800-53 Compliance Checklist and Security Controls Guide
Ensuring compliance with NIST SP 800-53 is critical for aligning your cybersecurity efforts with federal standards. This popular cybersecurity framework…
Read More » -
SERVICES

New Microsoft Exchange Server Vulnerability Allows Privilege Escalation to Admin
A significant security flaw, CVE-2025-53786, has been discovered in Microsoft Exchange Server hybrid environments. This flaw could enable attackers with…
Read More » -
TIPS

Navigating IT Certification Updates Effectively
Staying updated with certification changes is crucial for IT professionals looking to advance their careers. In this article, we will…
Read More » -
UTILITIES

Becky Holmes Knows Who *Isn’t* Dating Keanu Reeves
Becky Holmes loves DMing with scammers. When it comes to romance scammers, she will do whatever it takes, pursuing them…
Read More » -
SERVER

Does moving to the cloud mean compromising on security? — Matt Palmer
The transition to cloud computing is an evolution that many organisations are still undertaking to improve efficiency, scalability, and flexibility…
Read More » -
UTILITIES

Do I Need Antivirus App On Android Phone?
Do I need antivirus app on Android phone? Read on for the answer. Antivirus apps are known to provide extra…
Read More » -
COMMAND

Enhancing API Security with AI/ML: A Critical Imperative
Imagine this: A major retailer suffers a massive data breach. Customer credit card information, social security numbers, and purchase histories…
Read More »