UTILITIES
-

Your Protection Guide For Cybersecurity in Manufacturing
Cybersecurity in manufacturing businesses is unique. The sector faces several challenges that other industries don’t have to contend with. And…
Read More » -

‘Tis the Season for Holiday Scams
As the holidays approach, online retailers are ramping up discounts on hot-ticket items ranging from big-screen TVs to cookware. This…
Read More » -

Network Firewalls Comprehensive Guide For Non-Tech-Savvy People
This post will show you all you need to know about network firewalls. But before we proceed, let’s answer the…
Read More » -
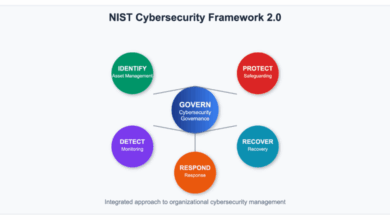
Why NIST CSF 2.0 Makes Sense for Mid-Market and Growing Businesses
Written by Brett Arion, Principal, Delivery Quality at Binary Defense Cybersecurity threats aren’t just a problem for large enterprises. Increasingly,…
Read More » -

Preventing Costly Data Breaches Requires a Robust Physical and Digital Security Posture
Independent market research firm Vanson Bourne recently conducted a study querying 1,000 senior IT decision-makers across the US and EMEA…
Read More » -

Make Phishing Training Count with HootPhish
Stop tricking employees. Start training them. Take Control of Your Security Awareness Training with a Platform That’s as Effective as…
Read More » -
Koske Malware Detection: New AI-Generated Linux Threat in the Wild
Attackers are increasingly leveraging AI to compromise critical business assets, signaling a dangerous evolution in the threat landscape. Check Point…
Read More » -
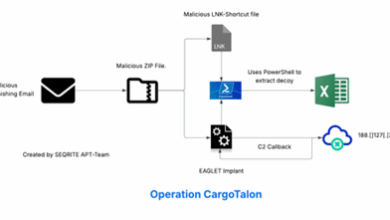
Ung0901 Targets Russian Aerospace Defense Using Eaglet Implant
Contents Introduction Initial Findings Infection Chain. Technical Analysis Stage 0 – Malicious Email File. Stage 1 – Malicious LNK file.…
Read More » -
Using Exposed Ollama APIs to Find DeepSeek Models
The explosion of AI has led to the creation of tools that make it more accessible, leading to more adoption…
Read More » -

What to Expect in 2025
2024 is coming to a close, and with it a banner year for cybercrime. Megabreaches that would have grabbed front-page…
Read More »