UTILITIES
-
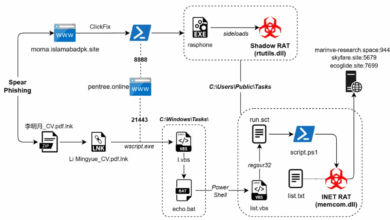
Espionage Campaigns Uncovered by Seqrite Labs
Seqrite Labs APT-Team has identified and tracked UNG0002 also known as Unknown Group 0002, a bunch of espionage-oriented operations which…
Read More » -
Jira Security Vulnerability CVE-2019-11581 | UpGuard
On 10 July 2019, Atlassian released a security advisory for a critical severity vulnerability in most versions of Jira Server…
Read More » -

The MSP Who Paid His Client’s Ransom and Tripled His Business
Most MSPs will tell you their worst nightmare is getting a call that a client has been breached. Dan Di…
Read More » -

Are Creatives Fleeing Instagram Due to AI?
Meta admitted last month that it was using content posted to its flagship platforms Facebook and Instagram to train its…
Read More » -

20 Best Cybersecurity Business Ideas For Entrepreneurs
Are you looking for the best cybersecurity business ideas? We have got you covered. Read on! Over half a million…
Read More » -
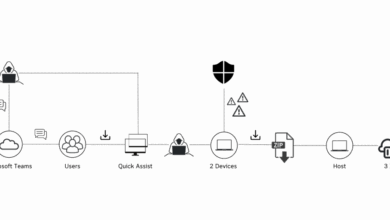
RMM: Tool Convenience and Control Comes with a Cost
Imagine this scenario: You’re winding down for the evening, having checked the locks and closed the windows, feeling secure enough…
Read More » -

Apple Alert: Critical AirPlay Vulnerabilities Expose Millions to Cyber Threats
A recent discovery by cybersecurity firm Oligo Security has unveiled a series of critical vulnerabilities in Apple’s AirPlay protocol and…
Read More » -
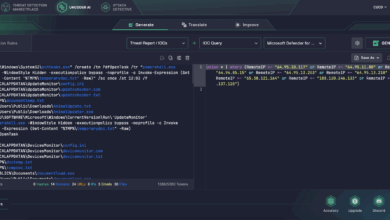
UAC-0099 Attack Detection: Hackers Target Government and Defense Agencies in Ukraine Using MATCHBOIL, MATCHWOK, and DRAGSTARE Malware
The UAC-0099 hacking collective, active in cyber-espionage campaigns against Ukraine since mid-2022, has reemerged in the cyber threat arena. The…
Read More » -
Android Cryptojacker Masquerades as Banking App to Mine Cryptocurrency on Locked Devices
The global craze around cryptocurrency has fueled both innovation and exploitation. While many legally chase digital gold, cybercriminals hijack devices…
Read More » -
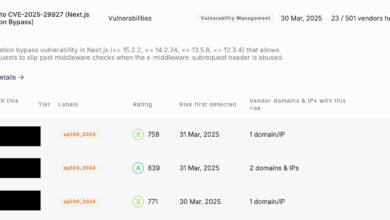
Critical Middleware Vulnerability in Next.js (CVE-2025-29927)
Researchers have discovered a critical security vulnerability in Next.js that allows attackers to easily bypass middleware authorization measures. The vulnerability,…
Read More »