UTILITIES
-
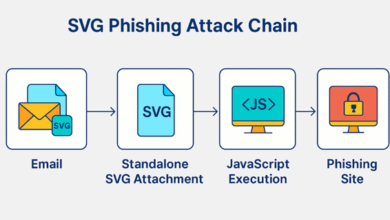
How Hackers Use Vector Graphics for Phishing Attacks
Introduction In the ever-evolving cybersecurity landscape, attackers constantly seek new ways to bypass traditional defences. One of the latest and…
Read More » -
NIST 800-53 Compliance Checklist and Security Controls Guide
Ensuring compliance with NIST SP 800-53 is critical for aligning your cybersecurity efforts with federal standards. This popular cybersecurity framework…
Read More » -

Becky Holmes Knows Who *Isn’t* Dating Keanu Reeves
Becky Holmes loves DMing with scammers. When it comes to romance scammers, she will do whatever it takes, pursuing them…
Read More » -

Do I Need Antivirus App On Android Phone?
Do I need antivirus app on Android phone? Read on for the answer. Antivirus apps are known to provide extra…
Read More » -

Multifaceted Cyber-Attacks Require a Unified Defense Approach
Gone are the days of attacks hitting a single product or vulnerability. Today, we’re seeing the increasing use of multi-vector…
Read More » -

How OAuth and device code flows get abused
Microsoft Entra ID, the identity backbone of Microsoft’s cloud ecosystem, is increasingly targeted through techniques like Device Code Phishing and…
Read More » -
Attack Surface Management Software: Top 10 Vendors
Key Takeaways: What is attack surface management? Why is attack surface management important? What are the best ASM vendors? Over…
Read More » -
Elizabeth Warren Tackles Big Tech
Elizabeth Warren put the kibosh on bad banking practices with her vision for the Consumer Financial Protection Bureau and now,…
Read More » -

A Look at a Novel Discord Phishing Attack
Written by ARC Labs contributors, Adam Paulina Binary Defense ARC Labs researchers recently investigated what appears to be a novel infostealer discovered in…
Read More » -

Neural Hijacking: Is Your Brain Making Security Decisions Without You?
Introduction: The Battlefield Inside Your Head In cybersecurity, we master firewalls and encryption. But are we neglecting the most critical…
Read More »