SERVICES
-
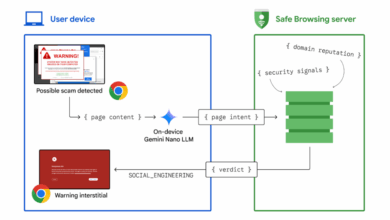
Using AI to stop tech support scams in Chrome
Posted by Jasika Bawa, Andy Lim, and Xinghui Lu, Google Chrome Security Tech support scams are an increasingly prevalent form…
Read More » -
How Can a Zero-Trust Approach Help Guard Against LLM prompt injection attacks?
How Can a Zero-Trust Approach Help Guard Against LLM Prompt Injection Attacks? As artificial intelligence becomes more embedded in business…
Read More » -

Top 6 VAPT Tools for 2024 You Should Know
IntroductionCybersecurity threats continue to evolve, making Vulnerability Assessment and Penetration Testing (VAPT) an essential practice for organizations. In this blog,…
Read More » -

EDR Meaning in Cybersecurity: Key Trends and Innovations
The cybersecurity field continues to expand with new acronyms and technologies appearing regularly. Among these, EDR has become one of…
Read More » -
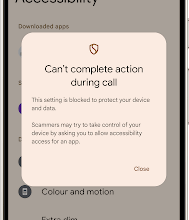
What’s New in Android Security and Privacy in 2025
Posted by Dave Kleidermacher, VP Engineering, Android Security and Privacy Android’s intelligent protections keep you safe from everyday dangers. Our…
Read More » -
LLM Cybersecurity: How Businesses Can Protect and Leverage AI Safely
LLM Cybersecurity: How Businesses Can Protect and Leverage AI Safely The rapid rise of artificial intelligence in business has brought…
Read More » -

The Role of EDR in Real-Time Threat Detection & Response
Understanding how EDRs work requires examining the sophisticated mechanisms that enable these systems to detect, analyze, and respond to cybersecurity…
Read More » -
Google’s Strongest Security for Mobile Devices
Posted by Il-Sung Lee, Group Product Manager, Android Security Protecting users who need heightened security has been a long-standing commitment…
Read More » -

Prompt Injection Attacks: Types, Risks and Prevention
Prompt Injection Attacks: Types, Risks and Prevention It’s no longer news that AI is changing how many businesses think. In…
Read More » -

Black-Box vs White-Box Penetration Testing Explained
Introduction When securing your applications, choosing the right penetration testing methodology is crucial. Two widely used techniques are Black-Box Testing…
Read More »