SERVICES
-

New Microsoft Exchange Server Vulnerability Allows Privilege Escalation to Admin
A significant security flaw, CVE-2025-53786, has been discovered in Microsoft Exchange Server hybrid environments. This flaw could enable attackers with…
Read More » -

Security Information And Event Management: Future Trends
The threat landscape for cybersecurity is changing at breakneck speed. Organizations are being bombarded with more creative attacks than ever…
Read More » -
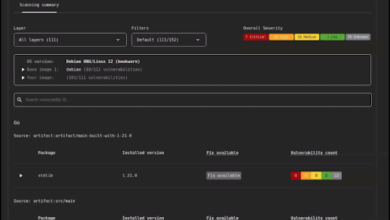
Vulnerability scanner and remediation tool for open source
In December 2022, we released the open source OSV-Scanner tool, and earlier this year, we open sourced OSV-SCALIBR. OSV-Scanner and…
Read More » -

Top 12 cyberattacks in the year 2023 : How organizations can prevent such attacks in 2024?
Contents Key facts of 2023’s data breaches January 2023: MailChimp Data Breach February 2023: Activision Data Breach March 2023: ChatGPT…
Read More » -

Mastering EDR Best Practices for Effective Threat Detection
Endpoint Detection and Response (EDR) solutions have become fundamental components of modern cybersecurity strategies. As cyber threats grow more sophisticated,…
Read More » -
Practical Model Signing with Sigstore
In partnership with NVIDIA and HiddenLayer, as part of the Open Source Security Foundation, we are now launching the first…
Read More » -
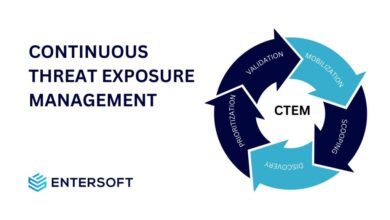
Harnessing Continuous Threat Exposure Management (CTEM) for Business Security
In the dynamic world of cybersecurity, Continuous Threat Exposure Management (CTEM) has emerged as a crucial approach for organizations seeking…
Read More » -

Google announces Sec-Gemini v1, a new experimental cybersecurity model
Today, we’re announcing Sec-Gemini v1, a new experimental AI model focused on advancing cybersecurity AI frontiers. As outlined a year…
Read More » -

Temporary Workaround for CrowdStrike-Induced Windows Outages
As you might be aware, there has been a major outage affecting Windows systems globally due to a recent update…
Read More » -

Top Features of Security Information and Event Management
Choosing the correct security information and event management solution can make or break an organization’s cybersecurity strategy. With cyber threats…
Read More »