SERVER
-
My Story from the Spanish Blackout
Hello Cyber-Builders 🖖 In 2017, I published a paper with NATO experts on what had happened to the Ukrainian power…
Read More » -
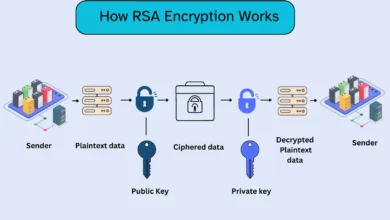
Enduring Power of RSA Encryption in Securing Network Communications
Introduction As organizations and individuals rely increasingly on digital systems to communicate and share sensitive information online, robust encryption methods…
Read More » -

Why We Must Embrace Risk and Learn From Incidents — Matt Palmer
Welcome to Incidentally: Why We Must Embrace Risk and Learn From Incidents As humans, we don’t take risks just for…
Read More » -

Speeding Up Vulnerability Remediation Through Threat Correlation in XDR
In cybersecurity, speed matters. But so does clarity. When your organization is facing hundreds or thousands of known vulnerabilities, not…
Read More » -

Why Nation-States Are Hacking the Power That Runs the World
“If you want to weaken a nation without firing a shot, start by flipping the switch.” Hello Cyber Builders 🖖,…
Read More » -

A Journey to the Highest Cybersecurity Maturity: Performance, Part 9
Activity Management Continue reading on The CISO Den »
Read More » -
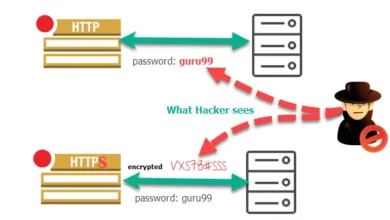
SSL Pinning Bypass with Frida and effective Mitigation techniques
Introduction In an era of unprecedented digital transformation, securing sensitive data and communications has never been more critical. One of…
Read More » -

thank you — Matt Palmer
Thank you to CSOonline for the CSO30 cyber security award this week. It’s much appreciated and a pleasure to be…
Read More » -

What to Look for in a Modern EDR Solution: 6 Critical Capabilities
The threat landscape now includes fileless attacks, zero-day exploits, and sophisticated lateral movements that evade signature based defenses. Basic antivirus…
Read More » -

A Journey to the Highest Cybersecurity Maturity: Quality, Part 10
Quality Management Continue reading on The CISO Den »
Read More »