SECURITY
-
Strategies to overcome the cryptocurrency scam
Cryptocurrency has revolutionized financial transactions, offering speed, anonymity, and decentralization. However, the rise of cryptoscams has become a significant concern…
Read More » -

Fake Job Interview Emails Installing Hidden Malware
Cyber criminals are becoming increasingly sophisticated, with a 60% rise in their use of deceptive tactics to infiltrate personal and…
Read More » -

What is DDoS attack: Types, signs, and how to
Companies face increasingly complex challenges every day, including cybersecurity threats aimed at disrupting their digital operations. One of the most…
Read More » -
Cybersecurity is changing how financial markets work but not in the way people think
People like to say that public markets don’t really care about security and that the impact of security incidents on…
Read More » -

Tips to make your summer travels cyber safe
Ready, set, pack! Summer travel season is here and that means family road trips, beach vacations, international adventures and more.…
Read More » -
Sharing Information with AI and Understanding the Risks
Artificial intelligence (AI) has become a huge part of our lives. From chatbots that answer questions to systems that help…
Read More » -

What Is Social Engineering in Cybersecurity?
How many times have you heard the phrase “don’t trust strangers”? The key point today is that many strangers disguise…
Read More » -
In security, not every industry problem is a business problem
Nobody can deny that there are many problems in our field. Just attend an industry conference or speak with five…
Read More » -

Black, White and Gray Box
Editor’s note: On the example of network security, Uladzislau describes the essence, pros and cons of black, gray, and white box…
Read More » -
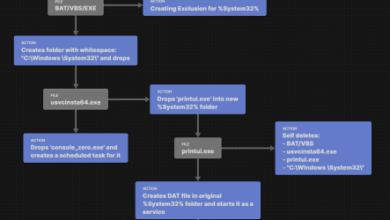
Hijacking Your Resources for Profit
Crypto Mining Crypto mining is the process by which individuals or organizations use computer power to solve complex mathematical problems,…
Read More »