SECURITY
-
Scaling Sophos to $1B+ revenue and defending the 350M overlooked businesses
In this episode of Inside the Network, we sit down with Joe Levy, CEO of Sophos, a 40-year-old cybersecurity company…
Read More » -

Smishing Scams Are on the Rise: How to Spot and
Text messages used to be a safe space—quick birthday wishes, delivery updates, maybe the odd emoji from a friend. But…
Read More » -

Zero Trust Explained: Why Traditional
Let’s face it—cybersecurity is no longer a game of building taller walls or thicker locks. The old rules, the ones…
Read More » -
When AI Voices Target World Leaders: The Growing Threat of AI Voice Scams
If someone called you claiming to be a government official, would you know if their voice was real? This question…
Read More » -

10 immutable laws of security, 25 years later
Back in 2000, the Microsoft Security Response Center released an article titled “10 Immutable Laws of Security“, describing what they…
Read More » -
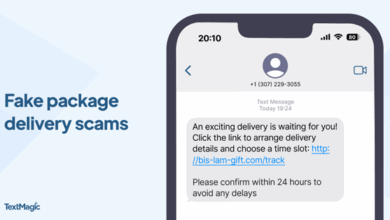
Mobile security matters: Protecting your phone from text scams
It all starts so innocently. You get a text saying “Your package couldn’t be delivered. Click here to reschedule.” Little do…
Read More » -

Cyber Attack on Japan Airlines Causes Global Disruptions
Japan Airlines (JAL), a leading name in global aviation, recently fell victim to a significant cyber attack. This breach disrupted…
Read More » -

What Is Malware? Types, Threats, and How to
The internet isn’t always a safe place. Behind every click, every download, and every flashy pop-up ad, there might be…
Read More » -
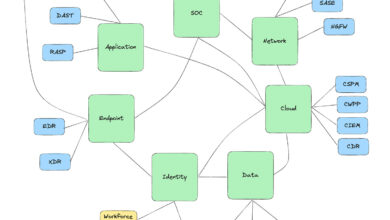
You don’t start a platform, you earn the right to become one
In cybersecurity, “platform” is the most abused word, used by every startup with two engineers and a feature flag. We…
Read More » -
IoT Penetration Testing Strategy
Gartner expects more than 65% of enterprises (for reference, it was only 30% in 2017) to adopt IoT solutions by…
Read More »