What CVE-2025-53770 Teaches Us About Zero-Day Reality and Ransomware Routine
CVE-2025-53770 is a critical SharePoint RCE flaw. It leverages unsafe deserialization and, when combined with one of several auth bypasses (CVE-2025-49704, 49706, or 53771), allows unauthenticated attackers to execute arbitrary code on exposed SharePoint servers. On paper, this sounds like a devastating new zero-day. But in practice?
We’ve seen this movie before.
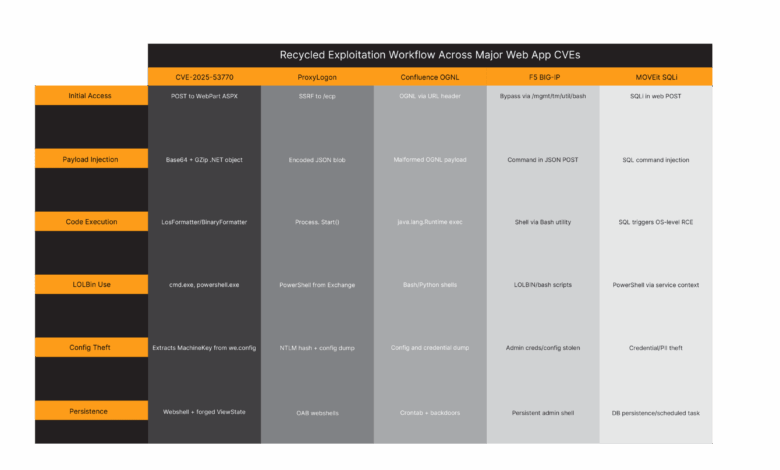
Drop the names, ProxyLogon, ProxyShell, Confluence RCE, F5 BIG-IP, and look at the tactics. The steps are familiar. The behaviors repeat. The tools barely change. The goals certainly don’t.
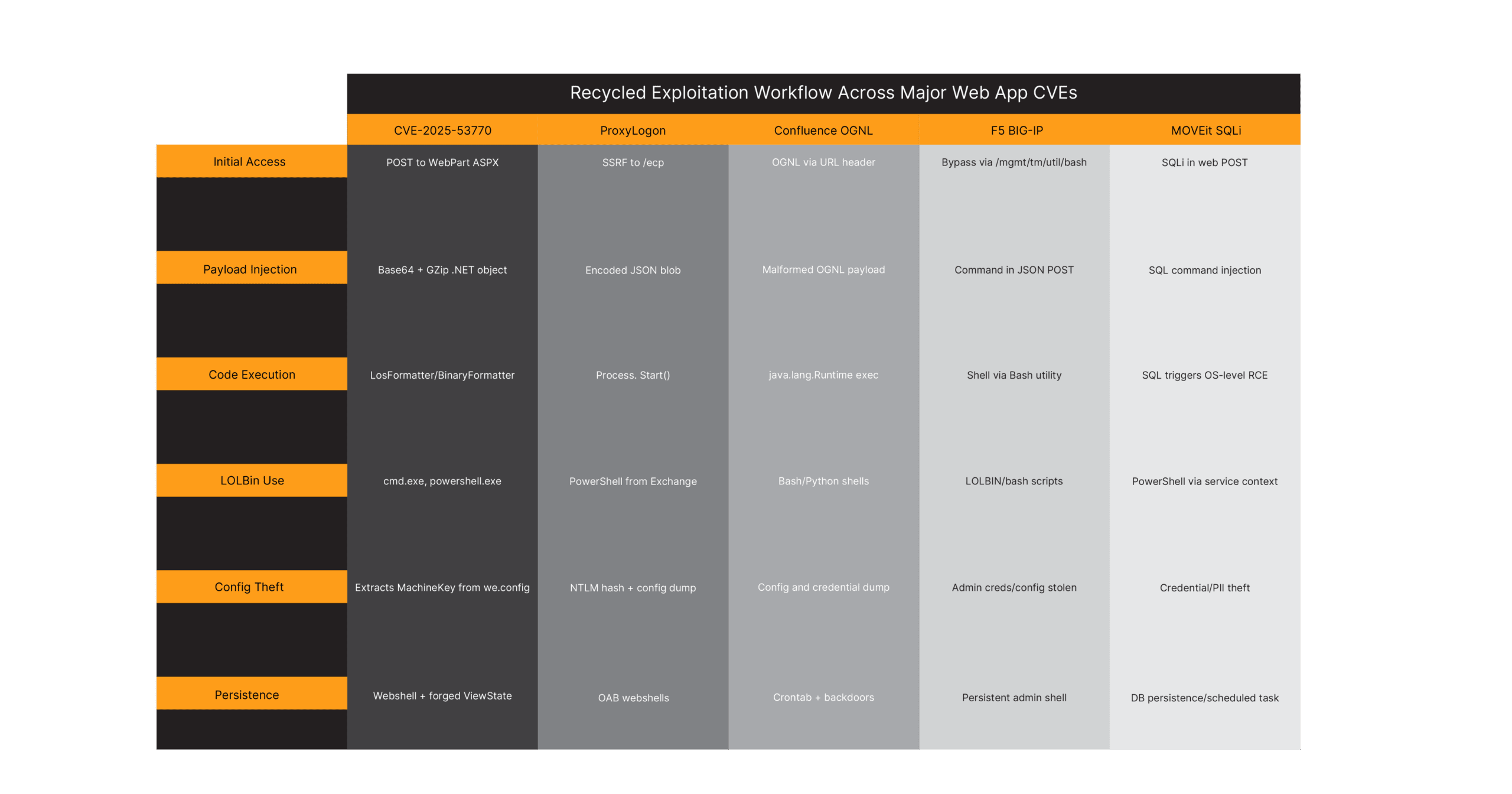
The latest exploit campaign using CVE-2025-53770 is a remix of a song we know by heart.
The Exploit Chain: Familiar Steps, Different Stage
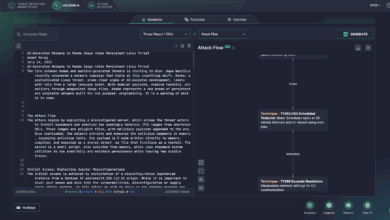
At its core, CVE-2025-53770 abuses how SharePoint handles WebParts, specifically how it deserializes compressed data embedded in payloads targeting endpoints like /ToolPane.aspx. The process is as follows:
Initial Access via WebPart Injection
- A malicious HTTP POST is sent to a WebPart-enabled ASPX page (not just ToolPane.aspx, any page with a WebPartZone will do, like /SitePages/test.aspx).
Payload Encoding
- The attacker crafts a base64-encoded, GZip-compressed .NET object using a gadget chain (commonly TextFormattingRunProperties via ysoserial.net), inserted into the MSOTlPn_Selected parameter.
Deserialization and Execution
- SharePoint processes the payload using LosFormatter or BinaryFormatter, invoking the deserialization sink and executing arbitrary code, typically starting with a LOLBin (cmd.exe, powershell.exe, mshta.exe).
Establishing Persistence
- The attacker drops a .aspx webshell into LAYOUTS (e.g., spinstall0.aspx), pulls MachineKey secrets from web.config, and creates signed ViewState payloads that enable sessionless, credential-less future access.
Sound familiar?
This exact progression, deserialization, LOLBin execution, persistence via web shell, echoes many major web application exploits of the last five years. The payload formats change, but the playbook doesn’t.
The Goals Haven’t Changed. Neither Have the Outcomes
On July 22, 2025, Microsoft published an article attributing attacks on SharePoint server leveraging CVE-2025-53770 to Chinese nation-state groups Linen Typhoon and Violet Typhoon.
While CVE-2025-53770 hasn’t yet been tied to ransomware (yet), it lines up nicely to ransomware operator objectives:
- Privileged access to enterprise data repository
- Privileged access to a domain-joined Microsoft Windows server
- Remote Command Execution
We don’t need to look back too far to see how the use of this exploit will likely play out.
ProxyShell and ProxyLogon began as zero-day vulnerabilities exploited by advanced persistent threat (APT) groups, most notably the Chinese state-backed actor Hafnium, to conduct targeted espionage campaigns against governments, think tanks, and defense contractors. In the early phases of exploitation, these vulnerabilities were used surgically by skilled attackers to gain stealthy access to high-value Microsoft Exchange servers.
However, within weeks of public disclosure and tooling release, the same attack paths were rapidly adopted by ransomware groups and access brokers. What began as APT-grade tradecraft was quickly operationalized for mass exploitation, leading to widespread webshell deployment, lateral movement, and ransomware incidents across enterprises worldwide.
Being able to align the goals and objectives of different threats and how exploits and vulnerabilities align to them is crucial to building a security strategy that is prepared for zero days.
Don’t Play Whack-a-CVE for Detections
Many orgs initially focused detections on:
- Requests to /ToolPane.aspx
- Dropped files like /LAYOUTS/spinstall0.aspx
- Referer headers spoofing /SignOut.aspx
However, based on testing within ARC Labs, there is some assumed brittleness to these detections. /ToolPane.aspx isn’t required. The referrer spoof is optional. Once the exploit matures, attackers will pivot to other ASPX targets. Path-based detection alone is brittle, just as it was with /owa/auth during ProxyLogon.
Instead, defenders need to ask:
- Is w3wp.exe spawning command interpreters or LOLBins?
- Are web applications writing script files to disk or modifying web.config?
- Are there indications of web shell activity in web logs?
- Are encryption keys or ViewState values being accessed?
Those are behavioral signatures. And they don’t care what the CVE is. Because the how these exploits manifest in terms of behaviors is the same. Again.
The Pattern Is the Point
CVE-2025-53770 is important. It deserves urgent attention. But it’s not surprising. And if it is surprising, that’s the problem.
Every time one of these zero-days hits, we treat it like a black swan event. But it’s more like déjà vu.
Attackers don’t need new tools because defenders are still slow to learn the old ones.
We’ve known for years that:
- Sharepoint, Exchange, and other Windows based web enabled services are high value targets
- Deserialization is a risky and recurring attack vector
- ViewState is abusable when secrets are compromised
- Initial access is more about exploiting behavior than code
None of this is new. What’s new is that we still wait for a CVE to start preparing.
Recognize the Pattern, Not Just the Payload
The industry often talks about cyber threats as if they’re constantly mutating, like some digital pathogen we can never quite pin down. But more often, they’re recycling playbooks that work because we keep letting them.
CVE-2025-53770 isn’t a curveball. It’s a reminder.
Ransomware actors, APTs, and access brokers don’t need cutting-edge tactics. They need unmonitored behaviors, unpatched servers, and brittle detections. They need us to keep responding to indicators instead of recognizing patterns.
So maybe it’s time we admit: the landscape may look different. But the terrain hasn’t moved.
The more things change, the more they really do stay the same.